Roles and permissions matrices are critical tools used to manage access control within an organization. Access control is an essential part of security management and involves the process of regulating access to resources and information within an organization. The process involves identifying users, authenticating them, and then authorizing them to access specific resources based on their roles and responsibilities.
A roles and permissions matrix is a document that outlines the various roles within an organization and the permissions associated with each role. The document is used to assign roles and permissions to users, define the access level of each role, and restrict access to sensitive information or resources. The matrix also outlines the specific tasks and functions that each role is authorized to perform, helping to ensure that users only have access to the information they need to perform their duties.
In the below Roles and Permissions Matrix example, role names are represented in the columns, and system operations are in the rows. Both the roles and the operations can be grouped for ease of reading.
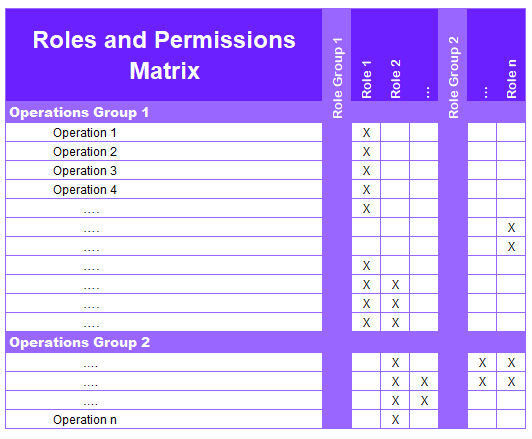

Overall, these matrices are essential tools for managing access control within an organization. They provide a clear and comprehensive overview of the access control system, help ensure compliance with regulatory requirements, enable auditing and monitoring of user activity, and promote the principle of least privilege. By using roles and permissions matrices, organizations can reduce the risk of security breaches, protect sensitive data, and maintain the confidentiality, integrity, and availability of critical resources.
One of the main purposes of a roles and permissions matrix is to provide a clear and comprehensive overview of the access control system within an organization. The matrix helps to define and manage access control by outlining the various roles within an organization and the permissions associated with each role. This helps ensure that users are only granted access to the resources and information they need to perform their duties.
These matrices are also valuable tools for managing compliance with regulatory and legal requirements. Many industries are subject to strict regulations that require organizations to protect sensitive data and maintain strict access control procedures. They also help ensure that organizations are compliant with these regulations by outlining the specific access controls in place.
In addition, a roles and permissions matrix is useful for auditing and monitoring access control procedures within an organization. The document provides a clear record of who has access to what information and resources, making it easier to track and monitor user activity. This helps organizations identify any potential security breaches or policy violations, enabling them to take corrective action to prevent future incidents.
Roles and permissions matrices also help organizations to implement the principle of least privilege. The principle of least privilege is a security best practice that recommends limiting user access to the minimum level necessary to perform their duties. By defining roles and permissions in a matrix, organizations can ensure that users are only granted access to the resources they need, reducing the risk of unauthorized access and data breaches.
Learn more about roles and permissions matrices, our requirements modeling language (RML®) and the many requirements models we use on a daily basis by navigating to the Requirements Modeling Language page of our website, or in our book Visual Models for Software Requirements (Microsoft Press, 2012) Joy Beatty and Anthony Chen. (See Chapter 11 for Roles and Permissions Matrix)