Many healthcare businesses unknowingly risk violating HIPAA protection laws due to critical weaknesses in the way they manage their patients’ sensitive HIPAA data. For example, a breach in the integrity of a single system within a HIPAA data network compromises the whole network–exposing both patients and companies.
What are the Risks?
The sensitivity of healthcare data is what makes those business such an attractive target of ransomware, which is becoming a multi-billion dollar industry. And if protecting patient data and fending off cyber pirates isn’t reason enough to take a hard look at security, when regulatory compliance is not standard across a network, HIPAA-related fines become possible. Fines can be very costly to businesses, with rarer penalties capable of reaching hundreds of thousands of dollars, or even in some cases exceeding a million. Additionally, procedures for capturing patient data, such as surgery filming or diabetic monitoring, present many challenges for meeting HIPAA regulations. For example, if healthcare procedures violate confidentiality and anonymity while capturing patient data, companies with secure networks still risk regulatory and legal repercussions due to the content they transmit. So how can healthcare businesses ensure their data networks and collection procedures are airtight and nearly invulnerable to breaches leading to HIPAA-related fines and lawsuits?
Use Modeling to Identify Vulnerabilities
Comprehensively mapping the data space of a healthcare process makes it possible to build confidential and user-friendly systems for clients. For example, as the ecosystem map below demonstrates, a typical patient scheduling process involves a surprising number of systems. A good ecosystem map can considerably aid health organizations in developing procedures for maintaining easy correspondence with patients while protecting their HIPAA information. An ecosystem map is a visual model that captures all the critical systems for a process and identifies data flow between them. For example, the ecosystem map below illustrates a common schema of applications involved in patient scheduling:
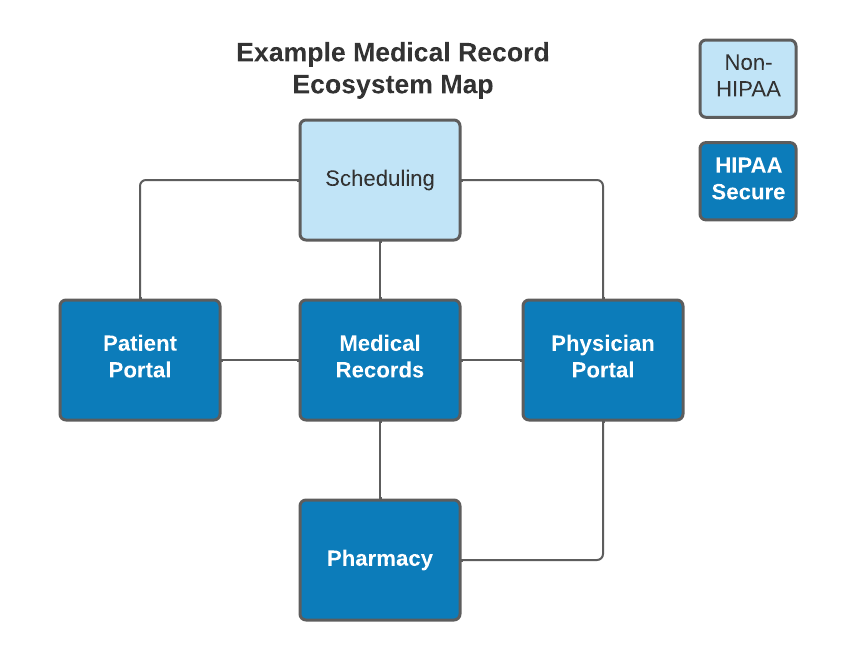
As the map illustrates, scheduling a patient involves direct touchpoints to systems containing sensitive data such as medical and pharmaceutical records. A quick-fix design for managing patient communication is to automate all messaging directly to their phones. However, such an approach would fail to comply with HIPAA regulations on data involving patient history or test results. A counter method could be to forgo direct messaging clients’ phones altogether by only using the patient portal for messaging. However, logging into a patient portal for all messaging results in a cumbersome client experience. HIPAA-safe messages containing appointment updates and reminders are best sent directly by phone where memory and logins are not required.
In this instance, the solution to optimizing the client experience is to use a tool such as an ecosystem map to determine which systems are a HIPAA risk. Designers can orchestrate processes that filter confidential messages to the patient portal and separately automate safe messages to patients’ phones when the data landscape is entirely in view. For real-world scenarios such as these, ecosystem maps illuminate data relationships and enable designers to make good choices when the interests and data of multiple parties are at stake.
Add Detail with a Data Flow Diagram
To really ensure data is contained within HIPAA secure systems, an Ecosystem Map can be paired with a Data Flow Diagram. In addition to the systems shown in the Ecosystem Map, a Data Flow Diagram details the flow of information between processes related to those systems. This is especially useful in healthcare to ensure that HIPAA-sensitive information never flows from a HIPAA-secure system to a non-secure system. For example, let’s take a simple action of a patient scheduling an appointment.
As described above, it can be burdensome to make a patient sign into a HIPAA-secure portal just to schedule an appointment, so it might be preferable to have the scheduling system be non-secure for ease of use. Likewise, it also provides a benefit to the physician if they can add notes/comments to an upcoming appointment for a patient, such as labs or procedures that need to be completed during the visit, so they can automatically be added to the patient’s medical records. However, medical notes are HIPAA-sensitive information, and cannot be stored in a system that is not HIPAA-compliant. When product managers or developers are looking at the feature level, it’s easy to see the need for this feature, and build it into a system without realizing the security implications. But when we look at the overall flow of information, it’s very quick to spot that there is HIPAA data flowing from a non-HIPAA process.
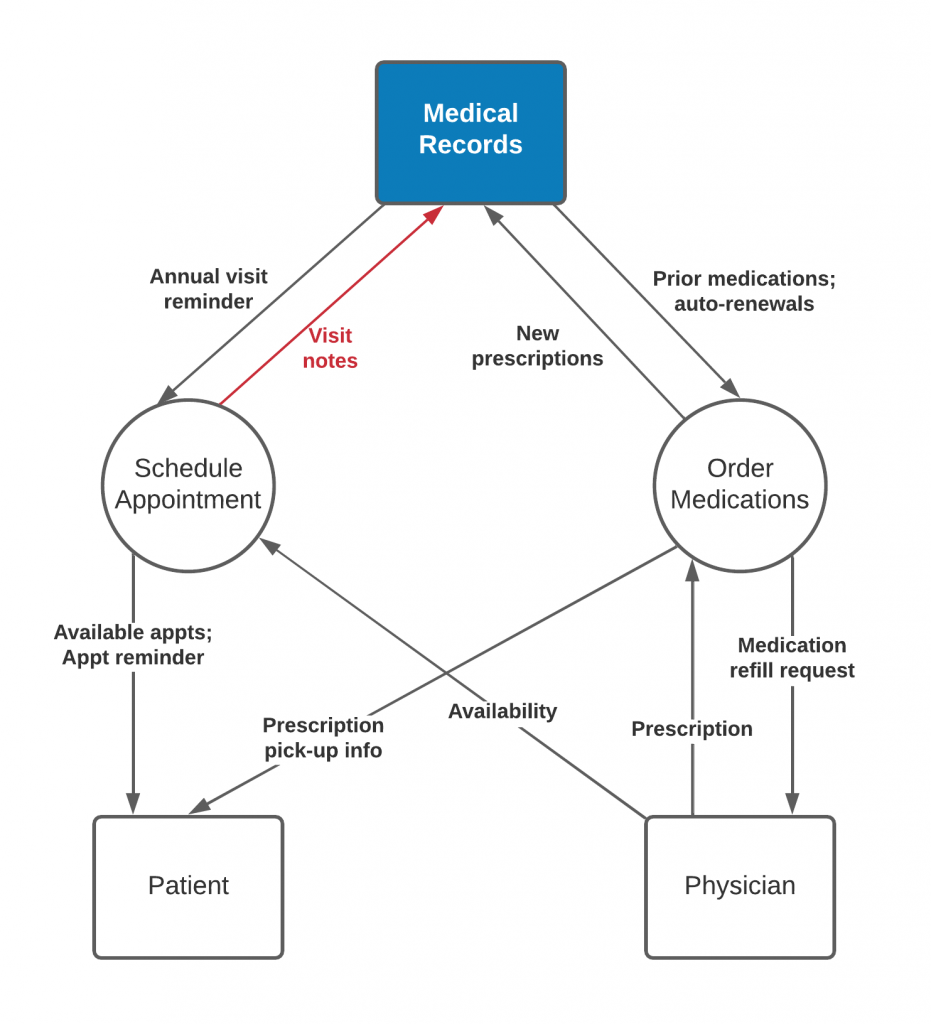
While healthcare is certainly not unique in its need for security, the complexities of the problems and the consequences of failures are significantly amplified. Visual models like an Ecosystem Map or Data Flow Diagram can be instrumental in simplifying that complexity and preventing issues such as security and HIPAA violations from occurring. And once HIPAA compliance is accounted for, then product managers and developers can focus on system usability without having to be as concerned about the risk those features may introduce, helping the physicians do what they do best—helping patients get better.